Hey folks 👋
I see you made it here again…drawn to the shadows just like me, so let me take you back for a moment.
When I first stepped into hacking, I wasn’t obsessed with exploits or payloads. I was obsessed with something far more unsettling - how hackers break people, not systems.
I remember trying to learn phishing purely out of curiosity - I wanted to see how deep the rabbit hole went. A friend of mine, a pentester, had access to a paid training course - I asked for his account - He said yes and that became my first backstage pass into how attackers really operate.
I learned how to craft convincing lures, how to automate the entire trap & how easy it was to set bait and watch people walk right into it. I tried it in a couple of safe environments and…yeah, it was disturbing - It was psychology with a keyboard.
And that moment pushed me to write this.
Most people don’t even realize they’re being played until it’s too late. So here’s your upgrade - a new lens to catch the con before the con catches you.
Let’s begin.
She heard a calm voice say “Hi, this is James from IT - we need to reset your password right now” She handed over a code. Five minutes later her company was dealing with a breach.
People assume hacking means green lines flying across the screen. But the easiest target is the person in front of the keyboard and today, with AI being able to mimic voices, write perfect phishing copy, and automate scams, these attacks are scaling faster than our defenses.
All this can be categorized as social engineering and it works because humans are predictable & vulnerable to pressure.
Read on and you’ll learn the main attack methods, real examples that work, and concrete, repeatable defenses you can apply right now.
What Social Engineering Actually is
At its core, social engineering is psychological manipulation with a goal: get you to reveal something, click something, or do something you otherwise wouldn’t. Attackers don’t always need technical skills. They need to be believable and patient.
And sometimes it’s not a stranger in a hoodie behind this attack; it’s people playing friendly, gaining trust, and then using that relationship to extract something.
Key features to watch for:
It targets different kinds of behaviors - Helpfulness, fear, and urgency….etc
Tactics often pair urgency with a purpose to push you into a quick decision.
Everyone’s a target - You may not be famous, but you hold data, access, or relationships someone wants.
In other words - Social engineering is subtle and scalable. With a convincing voice or message, a single attacker can compromise entire organizations. And motive isn’t always cash - some do it to spy on you, to prove a point, or simply for the thrill of breaking trust.
In short - social engineering is about who you trust, and when you trust them.
Trust is valuable. Some people use it to manipulate you, others to straight-up exploit you. There’s an entire business built on that exploitation - leeching off your trust. Read more on that here:
Seeing Social Engineering in Action
Now that you understand what social engineering is, let’s take it a step further. The best way to understand the danger of social engineering is to study actual incidents. These examples show how attackers use psychology to move through defenses that should be impossible to break.
Lapsus$ (2022) - Teenagers Outsmarting Big Tech
A group of teenagers took down half of Big Tech, not joking.
Lapsus$ got into Microsoft, Nvidia, Samsung, Okta, and T-Mobile. Their secret weapon was people. They bribed employees, socially engineered support staff, and even pulled SIM-swap tricks to hijack accounts. Once inside, they leaked source code, taunted companies on Telegram, and caused millions in damage - all without relying on sophisticated exploits.

This hack proves that - even the most secure companies in the world can fall if the employees aren’t fully equipped with what’s about to come.
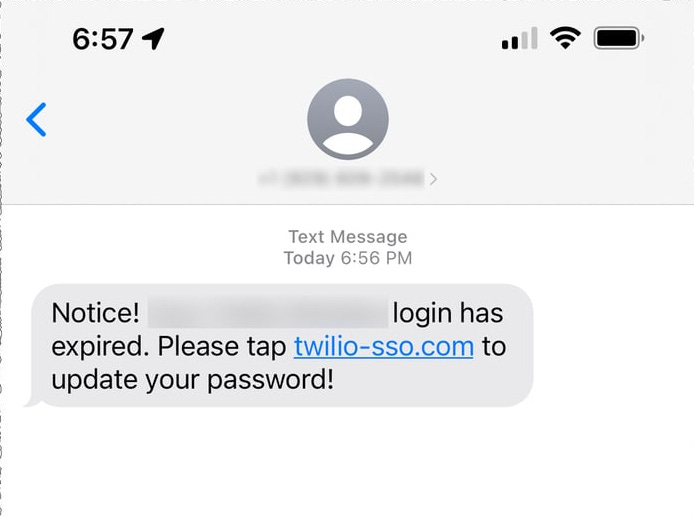
Twilio Phishing Attack (2022)
Attackers sent employees fake IT messages urging them to verify their login. The link looked convincing enough that multiple staff members entered their credentials. Those credentials opened doors to internal systems, giving attackers access to customer data.
Clicking on the link in the messages had taken unsuspecting individuals to a fake Twilio login page, where they entered their credentials and allowed hackers to gain access to customer data.
Now, after Twilio wrapped up their internal investigation, they confirmed something important. According to the company’s official statement, the same attackers had already pulled off a smaller breach weeks earlier by socially engineering an employee over a voice call:
“Our investigation also led us to conclude that the same malicious actors likely were responsible for a brief security incident that occurred on June 29, 2022. In the June incident, a Twilio employee was socially engineered through voice phishing (or ‘vishing’) to provide their credentials, and the malicious actor was able to access customer contact information for a limited number of customers.”
And once again, a social engineering attack proved that the systems aren’t always the weak point. The humans reading the message are.
What You Saw Above is Barely the Surface
The cases you saw above are nothing compared to the size of the real problem. Every year, companies, governments, celebrities, and everyday people get compromised by attacks that start with one message or one moment of trust.
If you want to dig even deeper, here are a few more social engineering incidents worth exploring:
How Attackers Learn Everything About You
Recon is where every social engineering attack begins. Before an attacker even talks to you, they study you. Every post & every about me line - it all becomes raw material. People forget that the internet never forgets.
In fact, OSINT is an entire skillset built around this. Attackers collect everything:
job updates on LinkedIn, vacation photos on Instagram, conference selfies, random tweets, even your contacts through “people you may know” algorithms.
Piece by piece, they build a complete profile of you - sometimes more detailed than what your own family knows.
And I’ve seen this play out - Some people post every single detail of their life online. Full diaries, daily routines, personal moments. Then when someone targets them, they cry, “How did he know so much about me”?
Simple - Because you told him.
Think Before You Post
Now, don’t get me wrong - this doesn’t mean you need to delete yourself, but be thoughtful and stay vigilant.
I get it - some info needs to be online. LinkedIn, professional achievements & that’s normal. But posting personal stuff without a good reason is how you turn yourself into an easy target. So, if you don’t have a legitimate reason to publish something personal, don’t publish it.
Why Anybody Can Be Tricked
You think a scam won’t work on you. So did a senior engineer who handed over credentials after a calm IT call. That’s the point - social engineering targets normal people who do normal things.
And most people assume - “That sort of trick won’t work on me” That belief is the root problem. This type of attack targets your instincts. Attackers find your blind spots and press them which is the main reason for its effectiveness.
Here’s an example - Banking apps verification calls - The caller claims your account is locked. They sound official, they pressure you, and they ask for verification codes. Many hand them over because the script mimics real bank procedures.
If you zoom out, you’ll notice the same key levers being pulled in every type of social engineering attack:
Authority - pretending to be your bank, boss, or IT.
Urgency - “Act now or you lose access”
Scarcity - “Limited offer, only for today”
Social proof - “Everyone else already did this”
Empathy - playing to emotions, fear, or sympathy
What You Can Do About It
You can start by slowing down by insisting on steps that slow them down (call-backs, formal requests). Then you can start relying on a trusted contact method or official website to verify if you are being played or not.
Other than that - you can limit your public exposure because the less they know, the harder it is to build believable pretexts.
How Platforms Accidentally Empower Scammers
Social engineering is not just about clever scammers - it’s also about the design of the apps you use every day. Platforms accidentally hand attackers the tools they need.
Example - Instagram’s $15 blue tick. It sounds harmless - until you realize that scammers use it to look official and most users don’t even know verification is buyable now.
And yes, Meta verifies with an ID
but only to ensure the buyer is a real person, not the identity they claim to be. This means - a scammer can impersonate a celebrity, verify their own face, and still run the fake persona.
The platform hands them instant credibility.
Dark Patterns: When Design Works Against You
Scammers love dark patterns because they work on autopilot. The whole idea is simple:
Make the dangerous option the easiest option.
Big Continue buttons.
Pre-checked boxes.
Urgent banners “Act now or lose access”
Layouts that hide the safe option behind tiny text.
Humans love convenience, we crave the path of least resistance, but that instinct gets weaponized against us. Once convenience becomes the default, your brain stops fighting back - especially when you’re already trapped in a dopamine loop the app created.
And that’s when scammers step in.
They bring their own tactics, their own dark patterns, their own psychological traps - but you’re already softened by the platform’s design.
You’re already clicking fast.
You’re already trusting the flow.
Put both forces together - the platform’s nudges + the scammer’s tricks
and boom: you end up doing exactly what the attacker wants.
And it’s not just scammers using these patterns. Platforms themselves rely on the same tricks to boost engagement, harvest more data, and keep you hooked. If you want to learn more about that, check out the following post:
How These Tricks Play Out in the Real World
Knowing the tricks is one thing. Seeing them deployed in real attacks is another and the best way to see their impact is to study real attacks where scammers used platform design to slip past people’s defenses. Following are some examples
that show just how easily these features can be turned against you:
The Blue-Tick Impersonation Scam
On Instagram and Facebook, scammers are buying the blue-tick and setting up profiles that look completely legitimate. The badge makes people drop their guard, so when the fake account sends a DM, a link, or a collab offer, users assume it’s genuine.
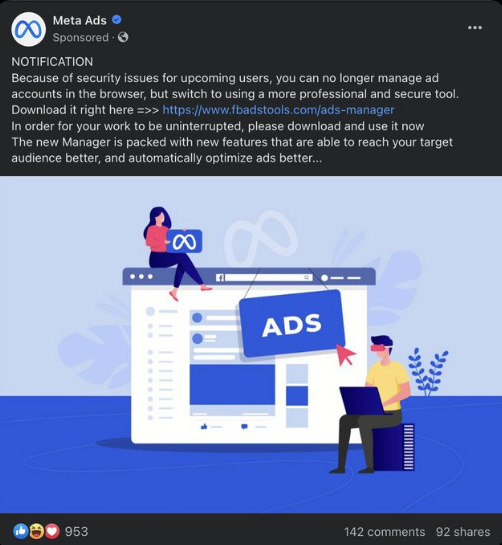
The trick works because Meta verifies the person holding the ID - not the persona they’re claiming to be. That gap lets scammers impersonate brands, influencers, or support teams with almost no friction. Victims trust the badge, click the bait, and often end up losing access, leaking info, or getting scammed before they even realize the profile was fake.
Fake Donation Campaigns
Scammers have been running fake donation campaigns across Instagram, Telegram, YouTube, and other platforms. They set up profiles that look like charity pages, post emotional stories, and add phone numbers or payment links to make the donation flow feel legitimate.
To make the campaigns look credible, they build networks of fake profiles to repost, comment, and vouch for the cause. This creates an illusion of legitimacy and social proof, pushing people to donate quickly.
How to Protect Yourself in a Rigged System
The only real defense here is a mindset shift: trust nothing, verify everything. Just because someone looks verified, has mutual friends, or seems perfectly legit on the surface doesn’t mean any of it is real. Scammers plan these details intentionally, and platforms make it even easier for them to blend in.
When something feels a little too smooth - stop. Step back, pull yourself out of the dopamine loop for a second:
Look at the message like an outsider
Ask if the timing, tone, or request makes sense
Most scams crumble the moment you stop reacting and start observing.
A small moment of skepticism can save you from a huge mess.
AI is Supercharging Social Engineering
There are countless branches of social engineering, and covering all of them in depth would take an entire book. But one thing needs to be crystal clear: AI has put this entire field on fast-forward. Attackers now use LLMs to create highly believable messages. They use voice models to imitate anyone in your contact list. They use deepfake tools to produce fake celebrity endorsements that spread like wildfire.

The Brad Pitt deepfake ad was just a small part of a much bigger system - It’s just one example of how easy instant credibility has become. If a scammer can borrow a Hollywood face in seconds, your brain barely has time to doubt it.
I’ll be doing a full breakdown of AI-powered attacks in a separate article - this is just a preview of what’s coming, stay tuned for that.
The Attacks Everyone Still Falls For
With the foundations in place, this is where we explore the actual mechanics of social engineering. These attack types show up everywhere…
In the next sections, I’ll explain some of the most famous methods in detail so you can recognize them when they happen to you.
Let’s get to it.
Phishing & Spear-Phishing
Phishing is when attackers send mass messages - emails, texts, DMs - that look official enough to make you click without thinking.
On the other hand - Spear-phishing is the evolved form of hyper-personal messages crafted just for you. AI has made this worse - Attackers can now generate emails that match your writing style, reference real coworkers, or clone internal templates.
The worst part is - everyone thinks they won’t fall for this - until they do and then… credentials get hijacked & malware gets inside the system.
You can visit Example Phishing Attacks to look at some practical examples, so you get an idea of what these types of attacks look like.
Pretexting
This one is all about the story. The attacker builds a believable scenario - an HR officer needing documents or a delivery guy asking for verification. The scripts are polished, the details feel legit, and the confidence makes you lower your guard.
Pretexting works because your brain reacts to the narrative before it questions it and the goal is simple - make you respond automatically to authority. Once that happens, the rest is easy.
Baiting
Baiting is one of the oldest tricks in social engineering, and it still works because it preys on curiosity & greed. The attacker leaves something tempting in your path - a free USB drive, a download link promising premium software, a leaked document. Once you take the bait, the attacker gets access: malware installs or ends up stealing your credentials.
Modern baiting happens online too - fake movie downloads, AI tool cracks - all packaged to look harmless but designed to infect your device the moment you open them.
A good example involves - Stuxnet USB Drop - Attackers dropped infected USB drives around Iranian nuclear facilities. Employees plugged them in out of curiosity, giving nation-state malware direct access to air-gapped systems.
Quid-Pro-Quo
Quid-pro-quo is a social trade-off attack. The scammer pretends to offer you something - technical support, discounts, upgrades and in exchange, they ask you for access or information. It’s the classic fake IT support call:
“We noticed an issue on your system; let me log in and fix it.”
Unlike baiting (which relies on curiosity), quid-pro-quo relies on our natural instinct to cooperate. That instinct blinds people, even smart ones, and hands attackers exactly what they need.
A pretty famous example involves - Fake Microsoft Support Scam - Attackers call pretending to be Microsoft technicians offering to fix a malware issue. Once the victim allows remote access, attackers install ransomware or steal credentials.
How to Defend Yourself Against This
The attacks I explained are just the surface layer. In reality - social engineering has countless forms - but they all rely on the same blueprint: pressure, emotion, and blind trust. But once you understand the blueprint, the attack loses its power.
Your defense is boring but effective
Don’t trust first - verify first.
Every scam succeeds because the victim reacted before thinking. Your job is to break that chain, slow the moment down, look at the context & Cross-check the claim through a separate, real source.
And yes, this applies to employees too. Attackers impersonate customers, vendors, even your own IT department to squeeze out data that isn’t theirs. Don’t hand over information just because someone sounds professional.
If you want your eyes opened even further, watch this clip - it’ll show you how easily people can be manipulated:
Defense Playbook - Hack-Proof Your Head
By now, you’ve already seen enough prevention tips across every section, no point repeating all of it. Instead, just keep in mind that hackers always find unique ways to attack you.
These attacks don’t only come from strangers. They can come from a cousin asking for a code, a coworker pretending it’s urgent, or someone playing friendly just long enough to slip past your guard.
So here’s the mental model that actually keeps you alive in the real world:
Pause → Verify → Only then act.
And if your emotions spike - that’s your signal to slow down, not speed up.
Quick Checklist - Screenshot This
When something feels even 1% off, fall back to this checklist. Treat it like your personal reboot button for weird situations:
Keep this checklist somewhere visible. When things feel blurry, this will help you wake up to reality.
If You’re Targeted - What To Do Fast
If you ever realize you’re being targeted, don’t panic. Slow down and switch into incident mode. Your goal is simple: contain → confirm → recover.
Step 1 - Stop responding:
Disengage immediately because it prevents further manipulation.
Step 2 - Save everything:
Take screenshots, save numbers, URLs, usernames - You’ll need them if you report it.
Step 3 - Confirm the truth:
If someone claims to be your bank, your friend, your boss - contact them using a trusted channel. Not the same chat.
Step 4 - Change your passwords:
Start with your main email. Then banking, socials, and anything that shares a password. After that make sure you enable app-based 2FA on all your accounts as well.
Step 5 - Inform the right places:
If it involves Bank, then - Freeze cards.
If Employer - inform them about it.
Friends/family? Warn them that someone may use your name next.
Local cybercrime office (if relevant)
Step 6 - Reset access:
Log out of all devices, revoke unknown sessions, update recovery numbers/emails.
The Final Truth
If you made it this far - respect. Most people don’t even last two paragraphs anymore.
But now you’re carrying something they aren’t - actual awareness.
You’ve seen how these attacks work. You’ve seen the psychology behind them and now you understand why even the smartest people fall for the simplest tricks. I’ve been in the trenches; I’ve watched basic scripts take down people who thought they were untouchable. Don’t be one of them.
With the passage of time, you are going to notice attackers & technology evolving.
But remember - the backbone never changes: social engineering still exploits the same human weaknesses. I’ve given you the fundamentals. No matter how shiny the new scam looks, the framework is the same.
And that checklist I gave you close to you. Carry it with you & most importantly actually use it - it will act as your protector.
Build mental friction & Guard your public surface.
Treat convenience as the silent enemy - it numbs the part of your brain that protects you.
Your Turn
Before you go - I want you to think about this:
What’s the last moment you “trusted by default” online and why?
Which emotion hijacks your judgment the fastest - urgency, fear, ego, or convenience?
Drop your answers in the comments - I want to see how you think.
If you want more content like this, hit subscribe and restack. I’m on a mission to help people see through the noise, and make them understand what’s going on behind the curtain.
But for this to reach more people, I need your support. Subscribes and restacks aren’t just numbers - they’re what keep this mission alive and spreading.
Dive Deeper
If you want to learn more, you can give the posts of different creators involving Digital-Mark, Erich Winkler, ToxSec on social engineering a read:










“Which emotion hijacks your judgment the fastest - urgency, fear, ego, or convenience?”
These days in convenience. It’s a hard urge to fight. I’m pretty aware of the tactics, like fomo and urgency, it’s the easy of use I slip on, when I’m not in full opsec mode.
Great post and thank you for mentioning me as well.
Still Social Engineering is another level of acting but used for nefarious reasons and lots of people are oblivious to it's inner workings.