Hey everyone 👋
Today’s topic is personal and honestly, long overdue. My interest in cybersecurity started years ago after watching Mr. Robot. That show was an eye-opener - It made me question about - how systems work, who controls them, and how fragile our security really is.
I started de-Googling my setup, reading the OpSec Bible, and trying to take control of my digital life.
Then came a conversation with my mentor that changed how I saw everything. He said:
“You can’t be fully secure when your data lives in someone else’s hands, because no matter how careful you are, one breach at a company you trusted and your private data’s gone”
Around that time, I was getting my national ID made and read about a major data leak that exposed millions of records. I realized I didn’t really have a choice, I was a part of the same broken system.
That’s when I decided to write this piece to explore what security really means in today’s world, and what you can still do to protect yourself.
Let’s get into it.
Have you ever wondered how secure your digital life really is?
Most people think they’re safe - they install antivirus software, avoid sketchy sites, keep their systems updated, and assume that’s enough.
But know that - you’re never bulletproof.
If you look closer, you’ll realize that - your personal data doesn’t live on your device anymore; it’s scattered across hundreds of systems and these systems are attacked every single day. Some breaches make headlines, but most never do.
And that raises the real question - how safe is our data, really?
In my eyes - Security is an illusion in many ways. It’s a performance that gives us comfort while real control rests in corporate hands - behind servers and networks we’ll never see.
The Bigger Picture: Everyone Gets Hacked
Everyone thinks they’re good at this ‘online security’ thing - strong passwords, open-source tools and sure, it’s a pretty good start.
But the truth is far more complex - your security doesn’t just depend on you. It also depends on the companies you trust - banks, cloud services, ride-sharing apps. And those companies get hacked a lot.
Millions lose personal data every year. Credit cards, phone numbers, ID copies - all floating around on the dark web. And what do most victims do? Nothing. Not because they don’t care, because they never had control in the first place.
Take the Tea app breach - just one of many small-scale leaks that quietly exposed user data. Now zoom out - Governments and corporations are rolling out digital ID systems that tie everything - banking, communication, healthcare - to one identity.
When that gets breached, it’s not just data that’s stolen - It’s you.
Anyway, that’s a whole other rabbit hole. You can read more about it here:
The Illusion of Control Starts with Trust
Know that - hackers don’t go around hacking random civilians, their eyes are on the big companies, and those companies are the ones to whom you hand your data over, trusting they’ll guard it better than you guard your own house.
And what do these companies, who “claim” to keep your data safe, do? They get breached, leak your info, or a lot of times sell it off behind the scenes without your consent.
So, maybe the real fight isn’t about your personal skill set - maybe…it’s about placing your trust in the wrong hands and systems.
Trust is powerful. In the right hands, it builds. In the wrong ones, it destroys.
There’s an entire business built around that trust - they all run on your belief that they’re on your side.
I actually broke this down in detail, how trust gets weaponized online, and how creators use it to exploit you. Give it a read if you haven’t already:
Breaches Aren’t Breaking News Anymore
Data breaches aren’t even rare events now. We’ve been watching this play out for decades, and if you think it’s getting better, the couple of years alone should wake you up.
All of them breached over the period, and this list doesn’t stop here, it can keep on going till I grow old, and the sad thing is it’s the same with every industry.
And the worst part is - You can do everything right: self-host your tools, firewall your toilet and you’ll still go down if one of these giants gets hit.
Because your data doesn’t live in your system, it lives in theirs.
That’s the trap: no matter how careful you are, you’re still connected to vendors and platforms that don’t owe you real protection.
Like the saying goes: ‘You’re only as strong as the weakest link in the chain.’
And in today’s world, that weakest link could be a forgotten database, an outdated PHP version, or a cloud service with a misconfigured permission.
The Human Factor
Hackers aren’t always cooking up some complex malware, like a scene out of Operation Triangulation, to pull off these hacks, making data breaches inevitable.
Most breaches happen because some random employee or even the CEO clicked a shady link, reused a password, or opened a malicious pdf document.
Take the Twitter 2020 hack - it was social engineering, not some god-level hack. A few well-crafted messages, and suddenly accounts of people like Elon musk, warren buffet were tweeting crypto scams.
That’s the point - you never really know who’s handling your data. One careless click from someone inside the company, and it’s game over. History is full of examples like this - not because systems failed, but because people did.
What Mitigations Exist and How Much Do They Help?
There are things you can do to tighten your personal security, usual things, such as: Two-factor authentication, password managers, privacy-focused browsers, all that good stuff. And yeah, they help a little.
Hell, you can even go full OPSEC mode, run everything through Tor, encrypt your life, but don’t forget:
Your ISP still logs you.
Data brokers still track you.
Companies you trusted still bleed your info.
So, how much protection are you really getting? Let’s break that down.
You Can Lock the Doors, But the House Still Has Windows
All of the usual security stuff does help at the individual level. It reduces your exposure, raises the bar a little.
But don’t mistake it for being bulletproof:
Take 2FA, for example: It works until someone SIM swaps you or tricks you into handing over the code, which is such a common thing these days.
We also got encrypted messaging, and it’s great…until you realize it only protects the content, not the metadata. Your ISP still knows who you’re talking to, when, and how often.
Maybe you run a VPN to hide from your ISP, but now your VPN provider sees everything and has all your personal details; now they have the upper hand on you.
Notice the pattern?
You escape one snake pit just to land in another.
What About Going Full Paranoid?
Let’s say you go all-in. Faraday cage phone pouch, Arch Linux - But then real life taps on your shoulder and you need to file taxes, order food, and apply for a visa.
Suddenly, you’re back in the matrix.
And even if you do everything right, you’re still not safe. One slip by your government and all your information, such as:
Phone number
Bank details
Email
Boom! Lying around on some dark web forum. At the end of the day - Neither your airtight setup nor any of your efforts to stay private mattered. You got dragged down by someone else’s failure.
And this is the part most people miss - your data footprint isn’t just what you control. It’s ISP logs, ad networks, third-party vendors, stuff you’ll never see, let alone secure
The Harsh Truth About Privacy
I think we can all agree that each and every one of us wants to take control of our lives, and even if we aren’t the ones with the control, we like to think we’re in control. We fool ourselves into believing that with the right tools and the right mindset, we can stay private.
but the reality is a bit weird, because this system was built to watch and track us.
I believe with all my heart that:
We can reduce the noise.
But complete silence?
That’s off the table.
So, maybe we should stop pretending that the web was ever ours to even begin with…
How Your Data Becomes Profit
When you are sitting on your sofa and using your favorite social media app, every click that you make, and every time you scroll - All of it is leaving behind digital residue. Even if you’re using privacy-focused tools, it still doesn’t completely protect your data from being:
Logged
Harvested
Sold & Repackaged
And, when the time is right, all of it gets exposed as well - This is surveillance capitalism in action.
Many of you might even be asking yourself: “Why do Governments even bother to spy on us”?
The answer is simple: It’s because they can. Similarly, corporations profile because it’s profitable. Hackers exploit because the doors are already open.
And none of this is accidental.
It’s a business model.
Anonymity is a Myth, and Consent is a Joke
It’s a myth that anonymizing your data keeps you safe. Re-identification is stupidly easy when companies have hundreds of data points on you. Sure, you can strip your name, but here’s something you can’t strip:
Behavior patterns
Typing styles
location
All these are fingerprint, and it doesn’t take much to link that back to you. And even if you manage to change all this, by the time you end up doing that - You will be inside another snake’s pit.
As for consent? That’s just a checkbox illusion. Privacy policies are walls of text that are designed so you don’t read them. Nobody really agrees with them and by the time regulators show up, your data’s already been mined and modeled.
Take Cambridge Analytica, for example. It was a manual, and everyone took notes.
So when a site says, “We value your privacy” what they really mean is: “We value your data and we’ll guard it just enough to avoid a lawsuit, until someone inevitably breaks in”
You’re Already Exposed: The Only Question Is: How Much?
In this modern era, almost everyone is online and that means everyone is exposed. That’s how life is now: you can’t opt out of the digital world anymore; the only thing you can do is manage your footprint.
The only question that matters now is: “How much are you willing to expose”?
Let’s not forget the folks who throw out the classic “I’ve got nothing to hide” That’s crap. Everybody has something to hide.
You need to realize that - that privacy is about control.
And if you’ve given that away, what do you really have left?
Accept It, or Go Off the Grid
The Truth is - You’ve got two options.
Option one - Accept the tradeoff. Know that using the internet means sacrificing a piece of your privacy every single time. It’s the cost of convenience. You can follow best practices, install blockers, and use privacy-focused tools.
But don’t fool yourself into thinking that makes you untouchable.
Option two - Go off the grid, delete your accounts, switch to cash and maybe build a cabin in the woods. Leave the digital world behind entirely.
The option number 2 isn’t for everyone, so if you aren’t someone who can’t opt for it, it’s totally understandable.
But that being said, just don’t walk around thinking a secure browser and 2FA is your shield. That’s like putting a lock on your tent. I know it’s hard to admit that you’re not safe.
But know that - you’re not alone. Everyone’s exposed. So instead of chasing perfect security, start building resilience and learn how to respond when things go sideways.
And if you’re into reading more about this - how digital safety really works under the surface - check out my other piece where I dive deeper into this rabbit hole:
Final Thoughts
Now, don’t get me wrong, privacy isn’t dead, it’s been taken, sold, and traded.
The actual warning is hidden in plain sight, and we keep agreeing to it without even reading it.
In reality, the Internet was built for connection and connection always comes at a cost.
You! yes, you! - Don’t slip into the victim mentality.
This isn’t about giving up or thinking everything’s pointless.
The point was to show you the reality, so you can actually play smarter.
Think of it like chess - sometimes you’re in a losing position, sometimes you’re in control, but no matter what, your job is to make the next best move. That’s how you turn the game around.
The same applies here.
You can’t control how tech giants handle your data, but you can control your own setup - Use app-based 2FA, a private browser, strong passwords, separate online identities, and sandbox risky actions.
Do what’s in your control because every smart move you make online compounds over time.
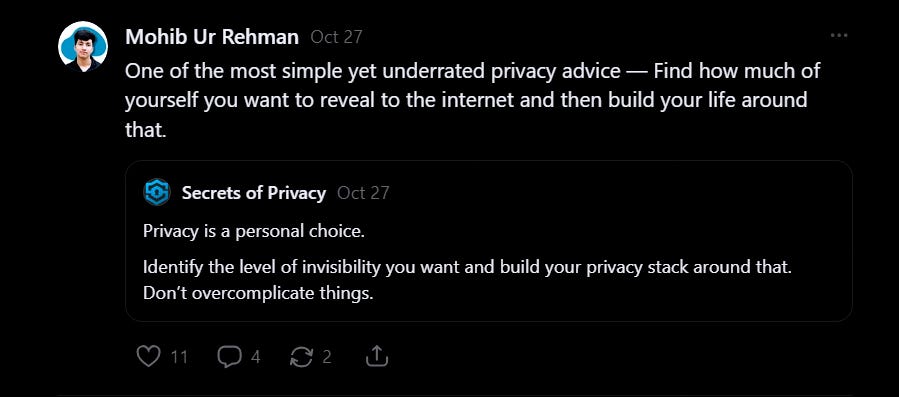
Credit goes to Secrets of Privacy for invoking this note’s idea in my brain:
And soon, I’ll be launching a free mini-series on how to actually solidify your online privacy. If this topic matters to you - you’ll want to stay tuned.
Your Turn
And before you go, ask yourself:
Are you really in control of your digital life…or just playing along in someone else’s game?
How much exposure are you actually okay with?
Let me know what you think in the comments.
If you want more content like this, hit subscribe and restack. I’m on a mission to help people see through the noise, and make them understand what’s going on behind the curtain.
But for this to reach more people, I need your support. Subscribes and restacks aren’t just numbers - they’re what keep this mission alive and spreading.







Great post, Mohib!
And no, I am not 100% in control of my digital life, but I am sure I am not the easiest target out there.
“Most people think they’re safe - they install antivirus software, avoid sketchy sites, keep their systems updated, and assume that’s enough.”
How true this is! Great writing thanks.