Hey there 👋
Great to have you here.
If you’ve been here before, you know we like peeling back the tech hype. We love to cover things for what they are, what matters, and what people never tell you.
Today we’re exploring how tech isn’t just tools - it’s culture, it’s identity, it’s the air we breathe.
So grab your coffee because today’s deep dive isn’t just another article - It’s a mindset check.
Say the word “hacker” and most people instantly picture some random guy in a black hoodie breaking into bank accounts.
But that’s only one version of the story - and honestly, it’s the wrong one.
At its core, hacking isn’t about crime at all. It’s about curiosity, creativity, and breaking limits. With the passage of time - the word has been twisted, but the roots are different.
It’s time to reclaim it.
Here’s what we’ll unpack today:
What the word hacker really means (and how it got hijacked).
Why hacking is a mindset that goes far beyond computers.
How people make an actual living by hacking - in ways that benefit everyone.
What a Hacker Really Is
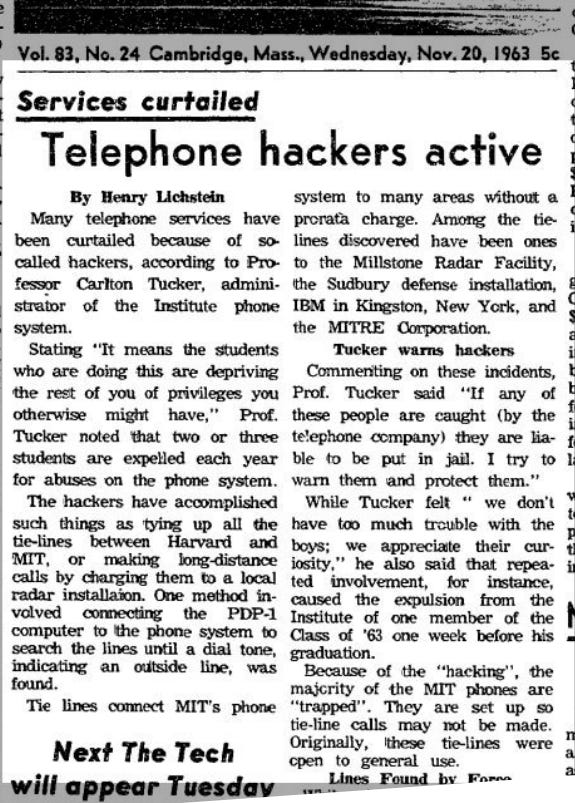
The word hacker wasn’t born in some FBI case file. Its first known print appearance in computing was November 20, 1963, in the MIT student newspaper. And back then, it meant something very different.
At MIT, students used the word hack to describe clever tricks, shortcuts, and creative solutions. It wasn’t about breaking laws - it was about pushing boundaries and finding unexpected ways to make systems do more than they were designed for.
One famous story comes from the world of phones. In the 1960s, curious students figured out how to hack the telephone system, using special tones to make free long-distance calls.
The essence of hacking was and still is - curiosity meeting creativity.
The Hacker Ethic: Curiosity, Exploration, Problem-Solving
What makes a hacker more than just a tinkerer?
The answer came in the 1980s, when Steven Levy published Hackers: Heroes of the Computer Revolution and gave shape to what’s now called the “hacker ethic.”
It was about a mindset, built on a handful of core principles:
Access to computers and systems should be unlimited and total.
All information should be free.
Authority should be mistrusted.
Hackers should be judged by their skills, not degrees or status.
You can create beauty and art with computers.
These are just some of the principles off the top of my head. Honestly, Hacker ethic is an entire worldview, and if you want me to do a deep dive on it, let me know in the comments.
But the heart of it is the following:
In a world dominated by algorithms and AI, it’s human creativity, curiosity, and collaboration that drive true progress.
Breaking the Hacker Stereotype
Have you ever noticed that when you hear the term “hacker” you instantly think cybercriminal? That’s no accident. That is the media pulling the strings because they decide what you think.
But that view is wrong - hacking ≠ crime.
Hacking is just power. And like any power, it depends on how you use it.
Think about it:
A phone can connect families or spread scams.
A knife can cook dinner or hurt someone.
Same tool, different intent - You’ve just been shown too much of the bad side, because the good side doesn’t make headlines.
The Hacker Mindset
I bet when you hear “hacking,” you immediately picture code and computers. But hacking goes far beyond that.
At its core, hacking is a way of thinking:
How does this system operate?
Can it be improved?
Can it be bent or repurposed in unexpected ways?
This can be applied to software, to businesses, even life itself.
People need to realize that - hacking isn’t about destruction. It’s about curiosity, reinvention, and rewriting the rules people take for granted.
Digital Examples of the Hacker Mindset
There are endless examples of hacking in the digital world. Following are just a few off the top of my head:
Reverse Engineering - To truly understand how a piece of software (or even malware) works, hackers take it apart piece by piece. It’s similar to dissecting a machine - breaking down its functions until every hidden part is revealed. This curiosity often leads to better security tools and new innovations.
Bug Bounties - Big tech companies literally pay hackers to break into their systems. Not to cause damage, but to spot flaws before criminals can use it to their advantage.
Zero-Day Exploits - Discovering a hidden weakness no one knew existed. Think of it as finding a secret door in a fortress before anyone else. Dangerous if abused, powerful if reported responsibly.
Real-World Examples of the Hacker Mindset
Even outside of computers, hacking shows up everywhere:
Apollo 13 Fix - When a spacecraft malfunctioned mid-mission, engineers hacked together life-saving solutions with duct tape and spare parts. A literal hack that brought astronauts home.
IKEA Hacks - people buying cheap IKEA furniture and reconfiguring it into custom bookshelves, or even hidden storage. This is reimagining what a product can do beyond its intended purpose - aka hacking.
And if you think about it - you’ve probably done it too.
Maybe you’ve found a clever workaround in daily life, maybe you crafted a resume packed with the right keywords to sneak different AI filter. That’s hacking as a mindset. Look closely enough, and you’ll see it’s everywhere.
Everything is Computers Now
There was a time when computers lived in labs and offices.
And today, they live in your pocket, your car, your home, and your city.
AI runs your smart home. Your watch tracks your sleep, your steps, even your calories. You’ve got earbuds in your ears. Even the car you drive is packed with computer systems managing everything.
And with every passing year, the line between human and machine is getting blurred.
Neural implants aren’t just sci-fi anymore - people are already getting chips in their brains and enhancing themselves with gadgets. What used to feel like cyberpunk fiction is slowly turning into reality.
But that’s a big topic on its own. We even covered it briefly in another piece - how humans and computers are starting to feel like one. If you’d like me to go deeper into that specifically, let me know in the comments.
Why does this matter here?
Because as computers are evolving, they are getting connected with us and that’s why hacking is becoming more than “those machines over there.” It’s becoming personal.
Soon, the systems you’ll be questioning, bending, or reimagining won’t just be devices around you - they’ll be extensions of yourself.
What do you think? Will humans and machines truly merge into one, or is that still science fiction?
My Hacker Origin Story
I was just another kid spending hours on video games, trying to escape reality.
Outside of games, I loved getting lost in movies and TV shows - especially the darker, more “schizo” kind of stuff.
Then one day, I stumbled onto Mr. Robot. And that was it. I was hooked and suddenly, the glow of a terminal looked more exciting than any video game.
It’s funny - ask around in folks in cybersecurity, and you’ll find an army of people who started because of that show.
But here’s the thing: most people never stick with it.
For the last few years, I’ve been digging into computers, joining communities, learning every day. Somewhere along the way, it stopped being about just “hacking” and became something deeper: a mindset, a part of me.
I often catch myself spotting flaws in university systems, finding shortcuts, thinking about how things could be bent - not to break rules, but to feed curiosity.
What about you? Everybody reading this probably has some story of how tech grabbed them. How did it start for you?
DEF CON – The Hacker’s Playground
Since we’re talking about hacking, it wouldn’t be cool if I didn’t introduce you to DEF CON.
DEF CON is the world’s most famous hacker conference, held every year in Las Vegas. Hackers, security researchers, and people who like to break things from all over the globe gather there.
It’s a mix of live talks, hands-on workshops, and legendary “Capture the Flag” competitions - where teams battle to hack into systems before others do. (Think of it like a digital treasure hunt, but for hackers.)
But it’s not just about competition. You get to meet like-minded people, share ideas, and even grab some pretty cool goodies and gadgets.
DEF CON isn’t just a normal event… it’s a whole damn experience and a culture.
I haven’t personally been there yet, but it’s one of my dreams. To walk into a room filled with the world’s sharpest minds and to see what it feels like to stand among the most elite.
And here’s something really cool:
Every year DEF CON hands out custom electronic badges. These aren’t just shiny name tags - they’re real circuits with hidden puzzles, and sometimes secret challenges built in. Badge hacking is a whole thing in itself.
Hacking Across Fields
Earlier, I mentioned that hacking isn’t just about computers. But I get it - that sounds a bit vague.
So let me walk you through a few examples where hacking exists outside of computers and is actively shaping the world.
Biohacking
It’s also known as human enhancement. It ranges from efforts to improve brain function to faster weight loss. Some methods are relatively safe at home, while others may pose health risks and produce varying results.
Take CRISPR, a gene-editing tool that allows scientists to rewrite DNA with incredible precision. In simple terms, it’s like cutting and pasting lines of code, but instead of software, the “program” is life itself.
And outside of labs, there’s even a DIY biohacking movement which involves people experimenting with biology in home setups, trying everything from implantable chips to self-made supplements.
Social Engineering
Social engineering is just a fancy way of saying hacking the human brain.
It’s not about breaking into computers - it’s about breaking into people. Out of all the hacking techniques out there, this one’s the most dangerous, because no matter how secure a system is, it’s only as strong as the person operating it.
Hackers use it to manipulate or trick others into giving up access. A phishing email, a fake phone call, or even just a well-crafted conversation - these are all social engineering in action.
There’s a quote that frames it perfectly:
“Amateurs hack systems. Veterans hack people.”
And like any big topic, this one is also a rabbit hole. If you want me to dive down in this particular topic - cover about what it is, how it affects you and how you can protect yourself - then do let me know.
Politics: Narrative Manipulation, Activism
Politics is the dirtiest kind of hacking there is. But let’s break down two of the most common ones.
Narrative Hacking
Think of politics as one giant operating system, where the “code” is public opinion. Whoever controls the narrative controls the system.
Example - Social media manipulation during elections. Fake accounts, bots, and targeted ads amplify certain voices while drowning out others.
This is hacking at scale by tweaking the information flow so people only “see” what you want them to see.
If you really want to learn more about how algorithms control your feeds and shape narratives, I wrote a whole piece on it: The Illusion of Choice: How Tech Decides Before You Do
Activism Hacks
On the flip side, hackers use the same mindset for good.
Example: The Arab Spring (2010–2011). Protesters bypassed government censorship with VPNs, proxy servers, and even video game chats to communicate with each other when platforms were blocked.
Hacking Has No Boundaries
What I just showed you are only a handful of real-world examples of hacking. In reality, it’s endless. Wherever there’s a system - be it biological, social, financial, or political - hacking can be applied.
But don’t confuse the mindset with morality. Hacking isn’t good or bad.
The intent is what turns it into freedom or manipulation, creation or destruction.
It’s never about the tool.
It’s always about the intent.
Hacking as a Career
We’ve talked enough about the mindset. But here’s something you might not know: hacking isn’t just about curiosity or creativity - it’s also a career. A real one. With real money.
Companies literally pay hackers to break into their systems, find weaknesses, and report them. Why? Because fixing those weak spots today costs way less than cleaning up after a massive cyberattack tomorrow.
This profession goes by the name cybersecurity. And inside it, hackers take on many different roles:
Penetration Testers → Paid “friendly attackers” who break into systems to show companies where the holes are.
Malware Analysts → People who dissect computer viruses to understand how they spread and how to stop them.
Security Researchers → Curiosity-driven hackers who look for flaws in software or gadgets and help fix them.
SOC Analysts → The digital security guards who keep watch on systems 24/7 for suspicious activity.
Bug Bounty Hunters → Freelancers who get cash rewards from companies for finding and reporting security bugs.
And this list is just scratching the surface.
Cybersecurity is a massive domain with countless branches.
If you want, I can even do a deep dive in a separate piece and break down each role, how it works, and what it takes to get into it.
But the point is this - notice how important hackers actually are?
Seeing the World Differently
Congrats, you made it to the end - here’s your digital candy 🍬.
Next time the word hacker pops up, you won’t just think “criminal.” You’ll know it means someone who questions, bends, and reshapes systems.
We all know different powers exist in the world - Hacking is also a power that can be attained. Some people use it for the good, while others use it for the bad - Hacking itself is not to be blamed.
And here’s the truth:
Nothing around you is fixed - It’s all puzzles waiting to be explored.
So next time someone spits the word hacker like it’s an insult, remember: curiosity built the world. And it’s hackers who keep pushing it forward.
Your Turn to Hack the System
Alright, I’ve talked enough. Now I want to flip it to you.
Imagine this: you’re a hacker, hired to find weak spots in your company, no matter how.
If you’re in finance, your approach will look different than someone buried in databases. Same company, different angles, different hacks.
But… it doesn’t matter from which department you belong to, the real question is:
What would “your” approach be?
Drop it in the comments - I want to hear how you’d think like a hacker.
If you want more content like this, hit subscribe and restack. I’m on a mission to help people see through the noise, and make them understand what’s going on behind the curtain.
But for this to reach more people, I need your support. Subscribes and restacks aren’t just numbers - they’re what keep this mission alive and spreading.
So if you found value here, back me up.
Let’s get more people aware, more people secure.
And hey, if you want to talk 1-on-1, don’t hesitate to DM me.
I’m always up for a good conversation.





Good read, learned tons of new things.
Firstly, nice post about the generality of hacks around us.
Another interesting thing is "All information should be free" is something which comes up in lot of fields and anything which pursues this is actually a noble cause. In economics it's the only way you can build stable societies cz money is inherently advantageous to earning more money. And whenever a system rewards winning, with tools which helps in winning more, it'll eventually drive a divide to the level of internal chaos. Free information is what breaks the shackle.