Hey There 👋
It seems that humans are some of the most creative when they are stopped from doing something. Take game hackers for example.
Anti-cheats debuted more than 20 years ago, but companies still spend millions in researching and coming up with new ways to stop cheaters in their games.
However some guys in their mom’s basement still win against these companies. Even two decades after, we still don’t have a perfect solution to preventing cheating in video games.
In 2025, tech is quite polarized already and kernel-level anti-cheat is a pretty controversial topic in-itself.
Instead of jumping on the hate band-wagon, I wanted to write about kernel-level anti-cheats, what they are and how they impact most gamers out there?
I am sure that most of us who have ever played multiplayer games, have at-least once played against a hacker. It's helpful when hackers are on your side but equally frustrating when they're playing against you.
It could be a guy with an aimbot, a guy flying in the air or someone shooting bullets at the sky and still getting perfect headshots. All of these people use clever tricks to bypass anti-cheats.
Cheaters and anti-cheat developers are always on the opposite sides of the ring. One is determined to get an unfair edge in games at any cost while the other works hard to bust the punks (pun intended).
These days we hear a lot of talk around kernel-level anti-cheats. Some people hate them while some have learned to live with them but the topic is still popular.
Last year's CrowdStrike incident that resulted in the largest computer outage in history has only added fuel to this conversation. A bug in their kernel-level security software literally halted the world.
That's why in this article, I'm going to shed some light on the mysterious 'kernel', how these kernel-level anti-cheats differ from traditional anti-cheat and how they impact us.
What’s an Anti-cheat?
Simply explained, An anti-cheat is a small piece of code whose job is to ban cheaters in video games. It detects and reports cheaters to the game developers for bans.
Anti-cheat software verifies game integrity and quietly scans the player's actions, and submits any unusual behavior that it detects to game developers resulting in bans for cheaters.
Anti-cheat software is usually bundled with video games and is itself a very small program that runs in the background analyzing the player's system as well as their gameplay to figure out if something's fishy or not.
Easy Anti-Cheat, VAC and Vanguard are some of the most popular anti-cheats out there bundled with games like Call of Duty, Valorant, CS2, etc.
Types of Anti-cheat
The use of anti-cheat software is not anything new. In-fact, anti-cheat software have existed in many forms for more than two decades now. The original Punk Buster (it’s an old anti-cheat software) released back in 2000.
Even though they share the same goal of detecting and reporting cheaters, two anti-cheats could be pretty different from each other. Largely, most anti-cheats could be divided into two categories:
Client-Side anti-cheat - This runs on the player's computer locally in the background analyzing behavior of the player on their own computer
Server-Side anti-cheat - It runs on the company servers and focuses more on how the player is behaving on the server
You could think of Server-Side anti-cheat as a security guard checking for your ID when you try to enter a building while Client-Side anti-cheat is a security camera that is placed above your shoulder by the game developer.
It should be noted that some companies also use a hybrid approach where they'll combine data from both the Server-Side and Client-Side anti-cheats to analyze if the player is cheating or not.
In this article, I'll largely talk about Client-Side anti-cheats that run locally on a player's computer.
Explaining The Kernel
So, most gamers use Microsoft Windows as their operating system. They install their games and the OS largely stays away from sight but hidden in the shadows is the kernel which is kind of a big deal.
You can think of the kernel as a bridge between a computer's software and hardware. Kernel is a highly privileged part of an operating system which has pretty much unfettered access to almost all areas of a computer.
We usually have standard user accounts on our computer for our daily work but sometimes when we're doing something sensitive like installing a new program we might need Administrator rights.
So, you can think of the kernel as a Super Admin that has the ultimate access to your computer's resources (be they software or hardware). It can do and see anything going on inside a computer.
What this means is that not only does the kernel have the most privileged access of a system but it is also one of the most sensitive parts of an operating system. Messing with the kernel can mean big trouble for the computer.
That's why most programs don't run in kernel mode because they don't need that level of access. They are run in user mode where the OS helps the program communicate with the kernel when they need it.
Most programs like video games don't need to communicate with the kernel directly and they just ask the operating system to do that through syscalls but some specific programs like graphics drivers and advanced anti-virus solutions do make use of the kernel level.
Explaining Kernel-Level Anti-cheats
As the name suggests, it is a type of anti-cheat software that runs on the kernel level, instead of the user-level that most programs typically run at. Just think of it as an anti-cheat running on God mode.
Running on the kernel-level means that these programs have pretty much entire control over everything that's going on inside your computer. They can see and manipulate most of what's running on the PC.
A program running on the kernel-level can see everything that one does on a computer all the way from daily browsing, media consumption to every other game and program you run.
So, the difference between a normal anti-cheat and a kernel-level anti-cheat is the level of access. The normal anti-cheat is confined to a set of spaces it can access and actions it can take but kernel-level anti-cheats don't have those limitations.
An operating system's kernel is a really sensitive place. So much so that a single bug can straight out crash your system and some bugs may even force you to reinstall your operating system or your programs altogether.
And this level of access is the point of many debates. You basically are giving up complete access to your computer to a game developer company.
Why Shift To Kernel-Level?
Taking anti-cheats to the kernel level has its share of benefits for catching cheaters. I'll discuss some of them down below:
Hackers Were Already There
Game hackers were the first ones to move to the kernel. They were the ones who found this as a bypass for normal anti-cheats. Conventional anti-cheats run on user-mode with limited access.
The hackers basically thought one step ahead and found that if they could get their cheats to the kernel-level it would mean that their cheats are loading even before the anti-cheat starts, this bypasses the anti-cheat altogether.
Running in user mode means that they have containerized access to a computer's resources just like most other programs. You have access to network, storage and processing resources that the OS allots you.
But if you take the cheats to the kernel-level now you have visibility over the anti-cheat itself and it's easier to develop cheats or fool off the anti-cheat which has limited access.
Since kernel-level programs have virtually complete control over software and hardware of a computer, this made cheaters win against conventional anti-cheat software running on user-mode.
So, this was more of a thing they had to do, to get to the level of cheaters. To catch cheats in the kernel required anti-cheats to go to the same kernel-level that the cheats reside in.
First Boot Privilege
Another reason for moving anti-cheats to the kernel was to start it before any other user-mode process could start.
Programs running in kernel mode start before the computer boots into the final OS. This means that the anti-cheat is running before other cheating programs could run and it could instantly identify and block execution for cheats.
Normal anti-cheats running in user-mode would be loaded after the kernel modules are loaded and because of this they couldn't identify cheats running on the kernel level.
This boot-level persistence is one of the major reasons for taking anti-cheat software into the kernel.
It doesn't matter if a program is running in kernel mode or user mode, programs running in kernel-mode can see every other process that is running on the computer.
Kernel-level programs can not just see but also edit the memory of any running program on the computer. This means that they can detect and straight out stop any execution that they detect as cheating.
This ability to see and manipulate kernel-level programs is key because many of the modern cheating methods that the cheaters use also run on the kernel-level.
So, when the cheats started to run in the kernel-level, anti-cheats had to follow them to the kernel. This makes life hard especially for cheat developers. Valorant has received much praise because of this approach.
Why Kernel-Level Anti-cheats are an issue?
As with most things in life, there are pros and cons to most things and that's certainly true for kernel-level anti-cheats.
The complete access to a computer's resources that a kernel has brings with itself a range of opportunities that one can use to shoot themselves in the foot. When you have complete control of a system it's pretty easy to break other software.
On one side, kernel-level anti-cheats have really made cheat developers' lives difficult but on the other hand it has raised some serious concerns, some of which I'm going to discuss below:
The Security Concern
A pillar of computer security is the concept of compartmentalization where you provide access according to the needs of a user. You limit access as much as possible so in the event of compromise the least amount of resources get affected.
This is why many in the cyber security community generally don't sit well with the idea of kernel-level anti-cheats because a single software having complete access to a computer means a single point of failure.
Another argument against kernel-level anti-cheats is that if these software do get compromised by an attacker, they can literally wreak havoc on the user and their computers without them ever knowing.
We've seen this happen where rogue employees have been successful in disguising crypto miners inside anti-cheats that were detected up till months.
All software has bugs and anti-cheats are no different. If an attacker is successful in exploiting vulnerabilities inside a kernel-level anti-cheat, it’s simply game over for the user.
Cyber criminals are always looking for high-privilege software as their next target. It would be a dream-come-true for a black-hat hacker to get access to a computer's anti-cheat and such people are already hunting for bugs in popular anti-cheats.
The Privacy Concern
The most vocal crowd that argues against kernel-level anti-cheats is the one that advocates for individual privacy and their arguments do have real grounds.
Running anti-cheat on kernel-level means that it has no-limits access to everything on a computer like browsing history, microphone’s input, all files across all users - basically everything.
And that is why many people are nervous with these hyper-invasive anti-cheats inside their system. You wouldn’t be comfortable if your building’s security guard has keys to each of the rooms in your house, no?
The Stability Concern
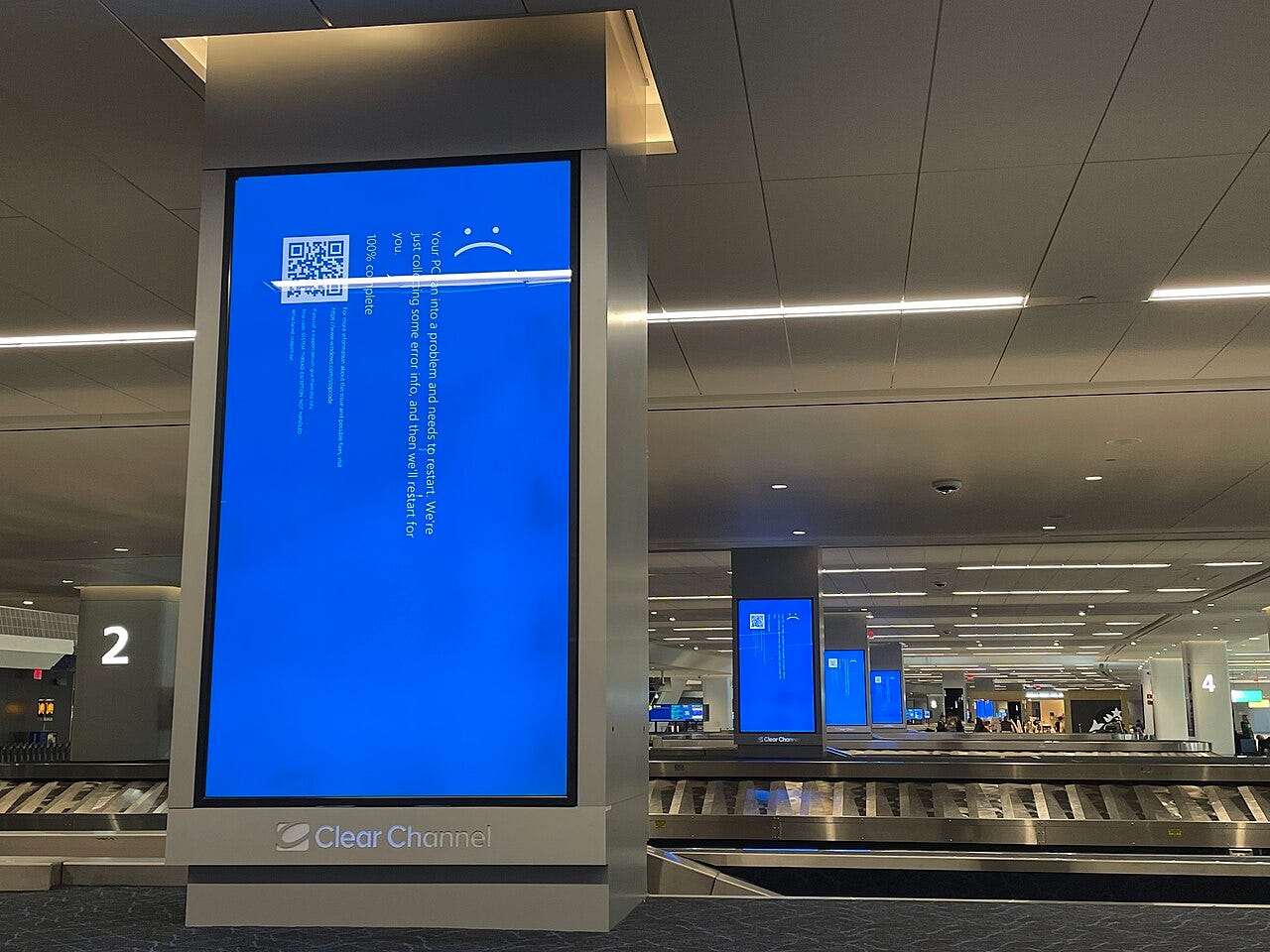
Just last year we experienced one of the largest computer outages in history when CrowdStrike released a bad update for their Falcon EDR.
Falcon EDR is a security solution that companies all around the world use to keep their computers safe from cyber criminals. You can think of it as a really advanced anti-virus that companies use.
Last year when CrowdStrike released an update for their Falcon EDR as usual, a single line bug crippled the better part of the world for hours just because their EDR runs in kernel-level.
Banks, Hospitals, Airlines were halted because of this update. Since the Falcon EDR runs on kernel level, most of these computers were showing the infamous blue screen of death and the fix was to re-image affected machines.
If you've made it here, here's something special for you. Below, I've shared a link to my article on the CrowdStrike outage going into the details of the incident:
CrowdStrike & The Tech World’s Balance – Greatest Outage in History
So, for kernel-level anti-cheats, people have the same concern, that a single bad update could crash millions of computers to the Blue Screen of Death at the least to permanently brick the computer's firmware at the worst.
What’s Next for Kernel-level Anti-cheats?
Kernel-level anti-cheats do work and they're pretty powerful but this doesn't mean that they are the only anti-cheat we have to make peace with.
We know that kernel-level anti-cheats aren't perfect and the gaming industry is working hard on a better solution. Many developers are using server-side analytics which flag players with impossible stats.
We are also seeing increased usage of AI-based detection systems including machine learning algorithms which are trained to find patterns between the behavior of a user and that of a cheater and report findings.
As we see more advancement in AI it is possible to see sophisticated AI implementations target to detect and hit cheaters with more accuracy and less trade-offs than kernel-level anti-cheats.
Some developers have also introduced peer rating systems. We are increasingly hearing talks of hardware-based anti-cheats that could be built directly into gaming hardware like CPUs or Graphics cards.
It is also possible that we may see hybrid approaches for cheat detection in the future that combine local AI-based detection with hardware level detection.
It is equally possible to have a combination of techniques like server-side validation, client-side detection and AI-based behavior analysis, all working together to hit cheaters.
As with most things in life, kernel-level anti-cheats present a trade-off. You get something but you lose something in return. Kernel-level anti-cheats are controversial but powerful.
There is no denying that kernel-level anti-cheats have made game cheating difficult. The stats support it. Cheaters in 2025 have to put significantly more effort to bypass kernel-level anti-cheats.
But still it can't be ignored that a single bug in these programs can crash millions of devices or cause permanent damage too. The privacy and security concerns can't be brushed off either.
The Road Ahead
After the CrowdStrike incident, Microsoft was grilled hard for allowing kernel-level access to security software and other software like anti-cheat in the first place.
Microsoft instantly promised (again) to lock down kernel-level access for stability so these incidents don’t happen again. The EU already pushed them once before to lock down the kernel.
If Microsoft is successful in locking down kernel-level access for Windows, it would mean an end to kernel-level anti-cheats too. Although the company has repeatedly shared intentions, any significant step is yet to be seen.
Hackers and developers' cat-and-mouse game doesn't seem to go off anytime soon. Cheaters are going to push harder for newer cheats and developers have to strengthen their defense.
Ideally we shouldn't have to trade our privacy and security to fight cheaters. Until Windows locks the kernel or someone builds a radically better detection method, kernel anti-cheats aren’t going anywhere. We can hate them. But they work (so far?).
I would love to know how you guys feel about Kernel-level anti-cheats. Do you actually prefer invasive cheats that bust cheaters or are you more concerned about them being invasive?
Whatever you think, do let me know in the comments. You can also rant about the anti-cheat you hate the most, comments are open to that too ;)